The U.S. government has officially accused Russia of an already well-reported effort to gain access to the country’s power grid, natural-gas and water pipelines, and other critical infrastructure control systems. But it hasn’t yet found any evidence that they’ve achieved those goals.
On Thursday, the Department of Homeland Security and the Federal Bureau of Investigation released a joint alert on “Russian government actions targeting U.S. Government entities as well as organizations in the energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors.” DHS and the FBI characterized this activity as a "multi-stage intrusion campaign."
The attacks, first reported in July 2017, started by targeting the business computing and information technology (IT) networks of power plants and other critical assets in these industries, using "spear-phishing," "watering hole domains" and other methods to gain entry, steal data, and spread malicious code.
But this was only the first part of a plan to gain access to operation technology (OT) systems, such as control systems for nuclear power plants and conventional fossil-fuel-fired turbines, that could be manipulated to cause equipment failures or blackouts.
Federal agencies were quick to respond Friday by announcing they’ve seen no sign of hackers succeeding in penetrating the targeted OT networks, which largely use legacy technologies that aren’t connected to the internet in day-to-day operations. Still, key policymakers from both sides of the aisle have called for increased efforts to combat Russian cyberintrusion into the power grid.
Energy Secretary Rick Perry told a congressional subcommittee on Thursday that he’s "not confident” the grid is secure from cyberintrusions, which are "literally happening hundreds of thousands of times a day. […] The warfare that goes on in the cyberspace is real, it’s serious, and we must lead the world."
Sen. Maria Cantwell, D-Wash., the ranking Democrat on the Energy and Natural Resources Committee, cited the alert as mounting evidence of a crisis that she first asked the Trump administration to address in March 2017, only to be “met with deafening silence."
"I hope today’s belated response is the first step in a robust and aggressive strategy to protect our critical infrastructure," she said in a statement.
The alert was issued by the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), which has documented attempts by Russia to access U.S. energy infrastructure starting as early as 2011.
But Thursday’s alert goes further into detail on the latest round of cyberattacks carried out since at least March 2016, most likely as a follow-up to an initial wave of intrusions reported in 2014. It also cited a report from cybersecurity firm Symantec, which ties the campaign to a group of hackers, code-named Dragonfly, which was behind earlier "reconnaissance" efforts starting as early as 2011.
This latest attack “targeted small commercial facilities’ networks where they staged malware, conducted spear phishing, and gained remote access into energy sector networks,” the report noted. But importantly, it didn’t start with the end target, but with “trusted third-party suppliers with less secure networks,” dubbed “staging targets.” Once these were penetrated, their networks served as “pivot points and malware repositories” for the next stage of attacks targeting the final, “intended” victims.
Among the targets of these final attacks were industrial control systems (ICS) or supervisory control and data acquisition (SCADA) systems running power plants, the report stated. And in some cases, the intruders were able to access workstations and servers on a “corporate network that contained data output from control systems within energy generation facilities,” including ICS and SCADA data.
That, in turn, gave them the ability to target and copy “profile and configuration information for accessing ICS on the network” -- in other words, the keys to logging into a network as an authorized user. DHS noted that it actually observed the intruders “copying Virtual Network Connection profiles that contained configuration information on accessing ICS,” including this user interface for a turbine control system, with the names of the companies involved redacted.
Targeting of ICS and SCADA Infrastructure
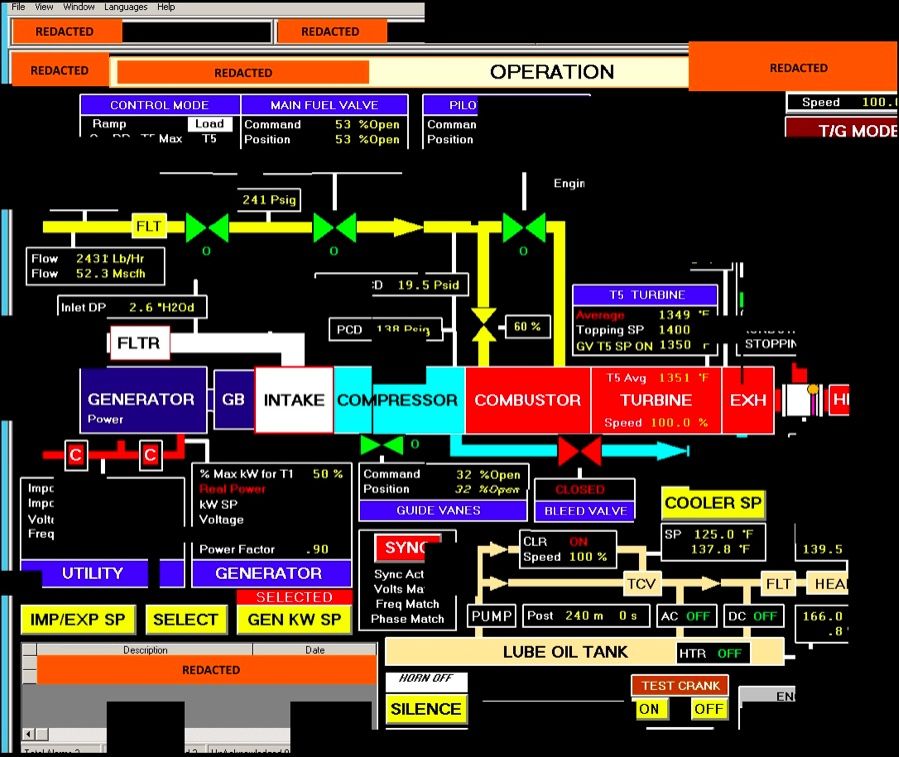
Source: U.S. Computer Emergency Readiness Team
Like most ICS-CERT alerts, this one contains “indicators of compromise and technical details on the tactics, techniques, and procedures used by Russian government cyber actors” to help the companies under attack to sniff out and expunge them from their systems.
The Nuclear Regulatory Commission said that “no safety, security or emergency preparedness functions were impacted” at the country’s 99 nuclear power plants, but that some corporate networks had been compromised. And the Federal Energy Regulatory Commission stated it had had no operational impacts on the country’s interstate transmission networks.
Scott Aaronson, vice president of security and preparedness at the utility trade group Edison Electric Institute, said that the federal government alerted grid operators to a threat targeting the energy and manufacturing sectors last summer, but that the incident hadn’t affected operations.
Still, cybersecurity experts warn that threats of this nature can lie undetected for some time, and are constantly being changed to adapt to counter efforts. They also warn that Russia is suspected of being behind two separate successful IT-to-OT cyberattacks that took control of power grid equipment and caused widespread blackouts in Ukraine, as part of its campaign aimed at supporting Russian separatists and sowing discord in the country.




