Let’s imagine an “improbable, but not impossible” cyberassault on the U.S. power grid. A shadowy group of skilled and malicious actors spend years implanting a piece of malware, dubbed the “Erebos” trojan, in the control systems of power plants across the Northeastern United States. It determines which of them haven’t yet installed hardware to prevent a type of cyber-enabled assault that’s been known to the industry for nearly a decade.
Then, on one fateful day, they activate the malware, causing up to 50 power-plant turbines to overload and burn out, blacking out the power grid between Chicago, New York City and Washington, D.C., and leaving 93 million people across 15 states without electricity. While some power is restored within 24 hours, it takes weeks for the rest -- and the cost to the U.S. economy adds up to $243 billion, or in a worst-case scenario, nearly $1 trillion.
That’s the scenario that “Business Blackout,” a joint report by Lloyd’s and the University of Cambridge’s Centre for Risk Studies, lays out for a utility industry that’s seeing cyberintrusions rise at an unprecedented pace. It also takes on the challenging questions of how to invest in protecting utilities against cyberthreats that are evolving as quickly as the defenses against them, if not more quickly.
Lloyd’s isn’t trying to play a scaremongering role here. “The Erebos Cyber Blackout Scenario is an extreme event and is not likely to occur. The report is not a prediction, and it is not aimed at highlighting particular vulnerabilities in critical national infrastructure,” the report’s authors state. “Rather, the scenario is designed to challenge assumptions of practitioners in the insurance industry and highlight issues that may need addressing in order to be better prepared for these types of events.”
Still, the report is not making up imaginary threats. In fact, the key method of disabling generators it describes was first revealed by an Idaho National Laboratory experiment in 2007, along with a video that showed how it caused a power turbine to burn out. Since that video was revealed by CNN that year, this vulnerability has been the subject of numerous studies and calls to action on the part of the industry.
Known as an “Aurora attack,” the method uses remote controls to open and close the generator’s rotating circuit breakers in quick succession, using the inertia of the generator itself to force the phase angle between supply and load out of sync. That can cause generators to overheat, and eventually melt down, catch fire or even explode.
Engineers involved with Aurora-attack mitigation noted in a 2013 article that hardware, such as Cooper Power Systems’ iGR-933 Rotating Equipment Isolation Device, or Schweitzer Engineering Laboratories 751A feeder protection relay, can monitor for out-of-phase conditions and isolate generators from their effects. The Lloyd’s of London scenario assumes that “most companies have updated their substation security, but not all, and 10% of generators remain vulnerable.”
As for how the hypothetical saboteurs would have gained access to power-plant control systems, the report lays out a number of well-known methods, including the “targeting of laptops and other personal electronic devices used by key personnel with routine access to multiple power plants; ‘phishing’ attacks designed to compromise the corporate network and pivot into the control system; hacking of remotely accessed control systems; [and] physical intrusion into locations used for network monitoring.”
The Lloyd’s report highlights that would-be cybersaboteurs would need to be quite sophisticated and careful to reach the level of undetected infiltration necessary to accomplish their simultaneous attacks on multiple generators. “Generating companies are fully aware of the possibility of cyberintrusion into their systems and have sophisticated security processes, personnel, and a system architecture dedicated to preventing it,” the report noted. “Usually, the control systems are separated from the general communications systems of the outside world by a firewall; places where information needs to transfer between the outside world and the control system are heavily screened and policed.”
Even so, the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team, or ICS-CERT, has documented cases of these kinds of intrusions, using “internet-facing hosts” such as laptops or PCs used to run utility control systems and SCADA networks. Late last year, ICS-CERT reported that a variant of the BlackEnergy malware had infiltrated power grid, oil and gas pipeline, and water distribution system control software.
National security experts told ABC News that Russian hackers were the likely culprit in this infiltration, which may have begun as early as 2011 and exploited General Electric’s Cimplicity control software platform. In 2012, Schneider Electric’s SCADA system was hacked by a Chinese group, according to experts. The Lloyd’s report lists a number of cyberattacks against industrial control systems stretching back to 1999.
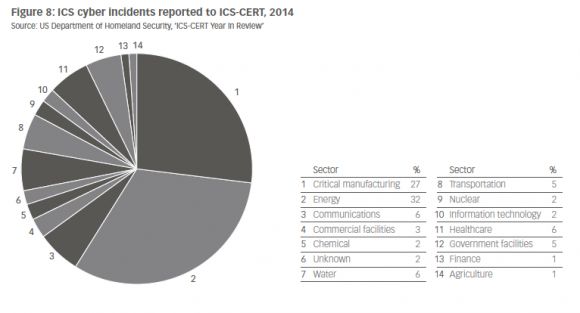
Attempts to penetrate utility IT networks are rising fast, making it difficult to weed out truly threatening intrusions against the flood of more run-of-the-mill events, such as data-theft attempts or hijacking of computing platforms to turn them into spambots. ICS-CERT reported that utilities topped the list of industries reporting cyberincidents last year, jumping ahead of critical manufacturing facilities and communications providers.
Most cyberintrusions are still directed at stealing data from public agencies, IT companies, financial institutions and retailers -- and the results of the worst cases of this type are of far more concern to a public that conducts much of their financial business online.
But industrial cybersabotage intrusions, such as the Stuxnet and Shamoon worms targeted at Iranian uranium enrichment and Saudi oil facilities, could be a much more severe threat to the infrastructure that keeps the modern economy running. The Lloyd’s report cites economic impacts including “direct damage to assets and infrastructure, decline in sales revenue to electricity supply companies, loss of sales revenue to business and disruption to the supply chain,” opening up the potential for claims paid by the insurance industry from $21.4 billion to $71.1 billion.
The proliferation of IT-connected systems like smart meters, distribution grid automation devices, and building energy control systems could expand the “vectors” of cyberattacks. Recent forecasts predict that utilities will spend between $7.25 billion and $14 billion on cybersecurity through the end of the decade, with much of that aimed at the SCADA networks and industrial control systems.
Still, it’s unclear whether the utility industry is up to speed on the scope of the cyberthreats it faces. A survey of more than 400 energy executives and IT professionals released last month by cybersecurity firm Tripwire noted that nearly half believed their organization could detect a critical-system cyberattack within 24 hours, and 86 percent believed it would take them less than a week, for example. But Tripwire, a subsidiary of communications and IT vendor Belden, noted other cybersecurity studies from FireEye and Verizon that found that most cyberintrusions on corporate networks took months to detect.